If you are an avid WordPress user, it’s very important to make sure your website is secure. One of the vulnerabilities that hackers often exploit is XML-RPC. Disabling XML-RPC can significantly enhance your WordPress security and protect your website from potential attacks.
But what exactly is XML-RPC, and how can it be a security risk? In this article, we will explore how to disable XML-RPC in WordPress and its common vulnerabilities.
Understanding the importance of WordPress security:
Since WordPress is the most widely used CMS, it’s a big target for online crooks. So, it’s really important to be serious about security to protect your website and its information. By following strong security steps, you can reduce the chances of bad people getting in, stealing data, or causing other problems.
Explaining XML-RPC in WordPress:
XML-RPC, which stands for Extensible Markup Language (XML) Remote Procedure Call (RPC), is a protocol that allows software to communicate with each other over the internet.
In the context of WordPress, XML-RPC enables remote access to your site’s functionality, such as publishing content, managing comments, and performing various administrative tasks.
Hackers can exploit XML-RPC to launch brute force attacks, which involve systematically attempting different username and password combinations until they gain unauthorized access. Bots can make multiple login attempts quickly, strain your server’s resources, and potentially compromise your site’s security.
Disabling XML-RPC can prevent such attacks and enhance your WordPress security. This can be achieved by utilizing security plugins, modifying your site’s “.htaccess file,” or adding code snippets to your theme’s “functions.php” file.
Common vulnerabilities related to XML-RPC:
While XML-RPC can be convenient for managing your WordPress site remotely, it also poses security risks. Here are some common vulnerabilities associated with XML-RPC:
- Brute force attacks: Malicious individuals may use these weaknesses to try to sneak into your site without permission by guessing or forcefully cracking passwords.
- Denial of Service attacks(DoS): It can cause your server to crash or become slow by flooding it with numerous requests, leading to DoS attacks.
- Information disclosure: It can leak sensitive information about your site, such as user data, which can be used for malicious purposes.
- Vulnerabilities in older versions: Older versions of WordPress had security flaws related to XML-RPC, making them targets for exploitation.
It is recommended to disable XML-RPC if you don’t need its functionalities. Disabling XML-RPC can be easily done using plugins or modifying your site’s functions.php file.
Understanding the potential security risks associated with XML-RPC and taking necessary precautions can ensure a safer and more secure WordPress website.
Methods to disable XML-RPC in WordPress:
Here are two effective methods.
- Using plugins to disable XML-RPC:
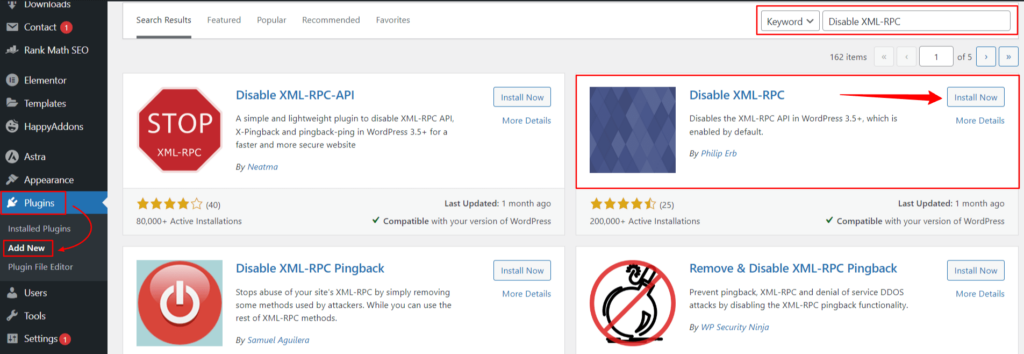
The simplest method is to use a plugin specifically designed to disable XML-RPC. Various plugins are available in the WordPress repository that can do the job with just a few clicks. Some popular options are Wordfence, Sucuri and Disable XML-RPC plugins, which can be easily installed and activated from your WordPress dashboard.
- Manually disabling XML-RPC in WordPress:
If you like to be more involved personally, you can also disable XML-RPC manually. This involves editing the “.htaccess file” or using a code snippet in your theme’s “functions.php” file. To edit “.htaccess file”, read this informative article.
It’s really important to create a backup of your website before making any changes so you can revert them if necessary.
To disable XML-RPC using the .htaccess file, you need to add the following code:
[<Files xmlrpc.php> Order Deny, Allow Deny from all </Files>]
Instead, you can insert the following code into your theme’s functions.php file:
[add_filter(‘xmlrpc_enabled’, ‘__return_false’);]
These methods will effectively disable XML-RPC on your WordPress website, enhancing its security. Don’t forget to keep your plugins and themes up to date, use strong passwords, and turn on two-factor authentication for extra security.
By implementing these measures, you can strengthen your WordPress security and enjoy peace of mind knowing your website is safeguarded against potential XML-RPC vulnerabilities.
Reasons to disable XML-RPC in WordPress:
- Prevention of brute force attacks.
XML-RPC can be vulnerable to brute force attacks, where attackers keep trying different logins until they break in, risking unauthorized access and your website’s security.
By disabling XML-RPC, you prevent attackers from exploiting this vulnerability, effectively thwarting their attempts to guess credentials and gain control of your site.
- Mitigating DDoS attacks.
XML-RPC can also be exploited to execute Distributed Denial of Service (DDoS) attacks on your WordPress website. By sending a large number of requests to your site through XML-RPC, attackers can overload your server and make your website inaccessible to legitimate users.
Disabling XML-RPC helps mitigate these attack vectors, protecting the availability and functionality of your site.
- Pingback and Trackback Spam.
XML-RPC allows pingbacks and trackbacks, which spammers can abuse to flood your site with irrelevant or malicious links, affecting your site’s credibility and SEO rankings.
- Enhancing overall WordPress security.
By disabling XML-RPC, you reduce the attack surface of your WordPress website. This means there is one less potential entry point for hackers to exploit.
Furthermore, since XML-RPC is not widely used anymore, disabling it does not impact the core functionality of your site.
However, it does provide an additional layer of security, decreasing the risk of unauthorized access or malicious activities.
Testing XML-RPC’s functionality after disabling:
As a website owner or developer, you may have recently disabled XML-RPC on your WordPress site for security reasons. But how do you ensure that the necessary functionalities are intact even after this disabling?
Here are the steps to verify if XML-RPC is correctly disabled and how to ensure that the essential functionalities of your website are not affected.
Verifying if XML-RPC is correctly disabled.
To confirm that XML-RPC is disabled on your WordPress site, follow these steps:
- Access your website’s admin dashboard and navigate to the “Settings” menu.
- Click on “Writing” and scroll down to the “Remote Publishing” section.
- If you find a checkbox labeled “Enable the WordPress, Movable Type, MetaWeblog, and Blogger XML-RPC publishing protocols,” ensure it is unchecked.
- Save your changes.
Once you have completed these steps, XML-RPC should be disabled on your site. To double-check, you can use a plugin like “Disable XML-RPC” to confirm that XML-RPC requests are blocked.
Ensuring necessary functionalities are not affected:
Although disabling XML-RPC enhances the security of your WordPress site, certain functionalities may rely on this protocol. To ensure that these functionalities are not affected, consider the following:
- Test website performance: Monitor the website’s performance closely after disabling XML-RPC to detect any negative impact.
- Check plugin functionality: Some plugins, like Jetpack, rely on XML-RPC for specific features. Make sure these plugins continue to function as expected.
- Test remote publishing: If you use remote publishing tools or apps, such as the WordPress mobile app, ensure that you can still publish and manage content without issues.
By following these steps, you can safely disable XML-RPC on your WordPress site, verify its disabling, and ensure that the necessary functionalities are not compromised. Regularly update your WordPress version and plugins to enhance security and maintain optimal performance.
Alternatives to XML-RPC for remote publishing:
If you want to enhance your WordPress website’s security, disabling XML-RPC can be an effective step. XML-RPC is a remote publishing feature that allows third-party applications and services to interact with your WordPress site.
However, it also presents a potential security risk, as hackers can exploit it to gain unauthorized access.
- REST API as an alternative to XML-RPC.
One alternative to XML-RPC is the REST API (Representational State Transfer Application Programming Interface). It is a newer and more secure method for remote publishing in WordPress. It provides a set of rules and conventions for building and interacting with web services.
It offers functionalities similar to XML-RPC, allowing you to perform tasks such as creating, updating, and deleting posts and retrieving user information. It also provides additional features, like improved performance and better support for modern web technologies.
Exploring the benefits of REST API:
By using the REST API instead of XML-RPC, you can enjoy several benefits for your WordPress site’s security:
- Enhanced security: The REST API prioritizes security, following modern best practices and ensuring robust protection for remote publishing.
- Improved performance: Built on cutting-edge web tech, it is faster and more efficient than XML-RPC, boosting your website’s overall speed.
- Compatibility: The REST API integrates with various apps and frameworks, simplifying connections to different services and systems.
- Future-proofing: Choosing the REST API keeps your site current and aligned with WordPress advancements as XML-RPC usage declines and faces potential deprecation.
You can boost your WordPress site’s security and keep the perks of remote publishing by turning off XML-RPC and using the REST API instead.
Conclusion:
By disabling XML-RPC on your WordPress website, you can significantly enhance its security and protect it from potential vulnerabilities. This simple step can prevent unauthorized access, brute force attacks, and other malicious activities.
